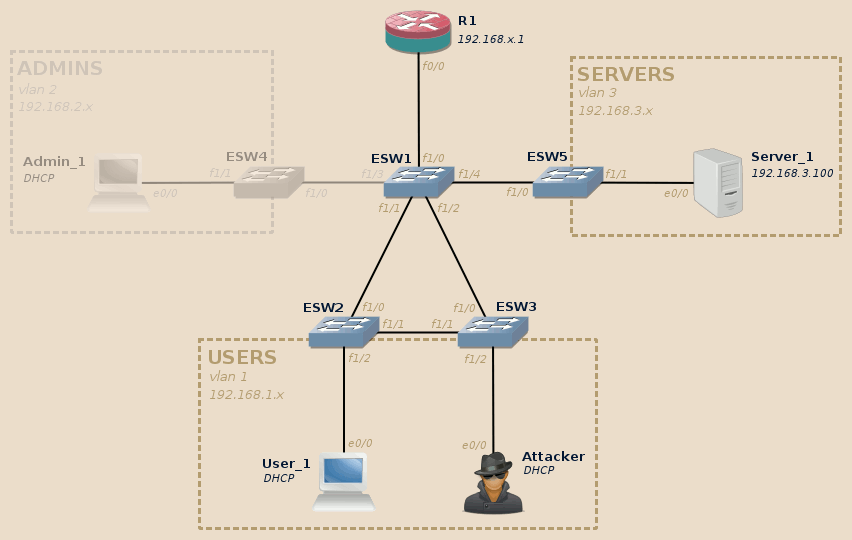
As we saw in the previous post, Wireshark revealed us the presence of STP messages.
The Spanning Tree Protocol is used to detect topology loops and build the most efficient forwarding path between interconnected switches. Topology loops are not a mistake but a way to add redundancy to a topology. Would a link break, the STP protocol detects it and recalculate a new most efficient tree.
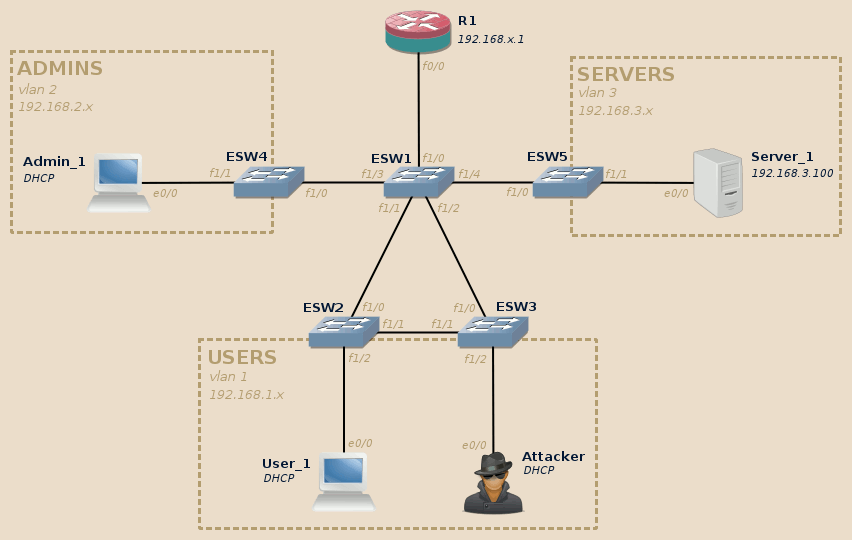
In sane networks, access ports should not deliver STP messages to end-devices, but this is not the default and, as Wireshark told us, not the case in our lab. This lets the attacker the possibility to simulate a topology change by sending maliciously crafted STP messages.
For this lab we will need at least the User_1 and Server_1 devices to be available:
Warning
The support of STP in the IOU images I tested was very buggy, STP port state was ignored and frames systematically …